Interview with Mr. Jan T. Peters, Managing Director of E-quipment BV
Share
September 19, 2019 - Mr. Jan T. Peters, Managing Director of E-quipment, gave an exclusive interview to Epicos . Among others, he stated that: “E-quipment is exclusive distributor of iStorage data and cloud security products in the BeNeLux area. We sell a complete portfolio of secured portable encrypted storage solutions, protected by PIN, and accredited by the Dutch Government and NATO. We focus on endpoint protection, and soon we are providing E-equipment Cyber Security training from an online portal.”
Mr. Peters, would you like to describe the current position of E-equipment in the national and international markets?
E-quipment is exclusive distributor of iStorage data and cloud security products in the BeNeLux area. We sell a complete portfolio of secured portable encrypted storage solutions, protected by PIN, and accredited by the Dutch Government and NATO. We focus on endpoint protection, and soon we are providing E-equipment Cyber Security training from an online portal.
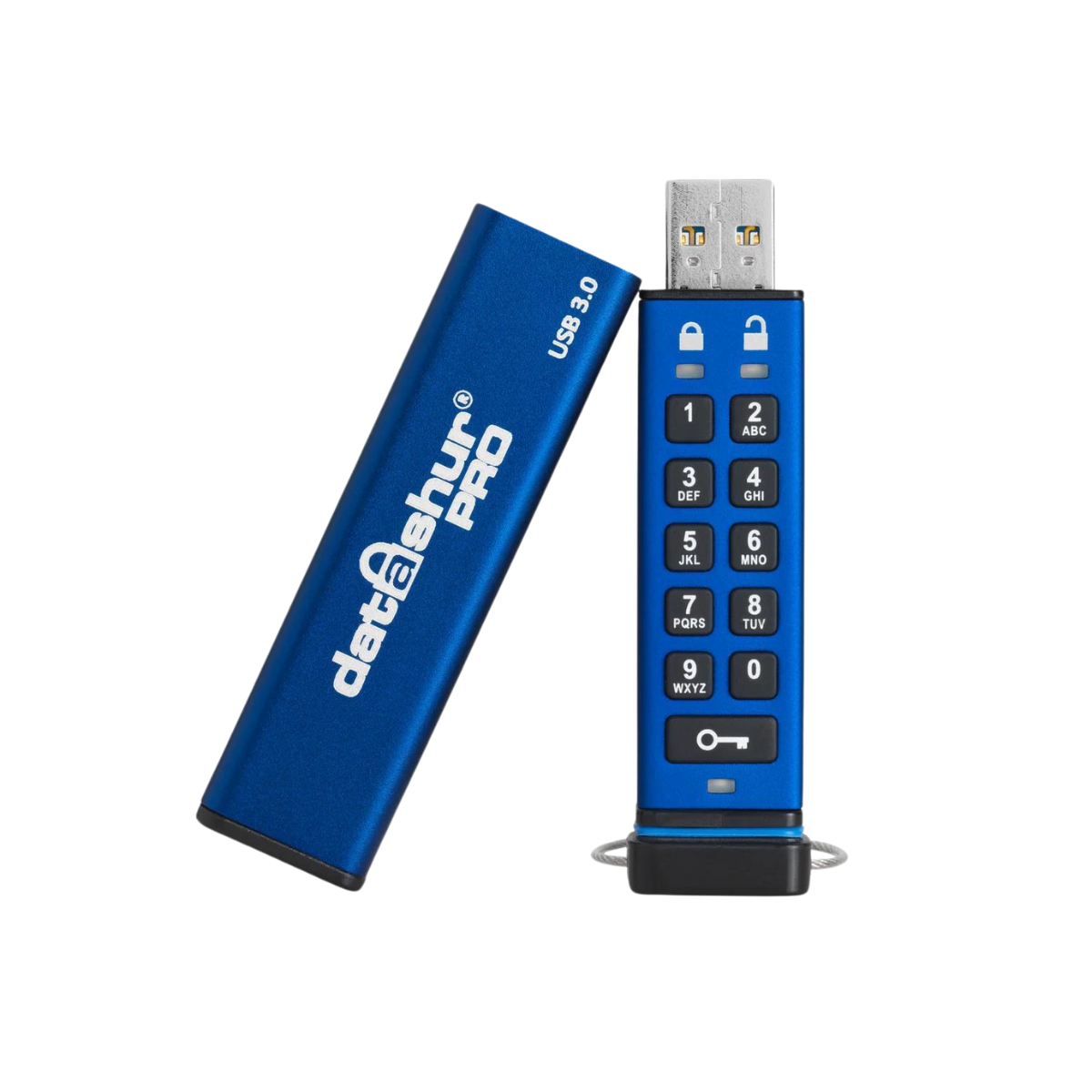
E-quipment has recently launched two new products, datAshur Pro2 and cloudAshur and we would like to know more about them. Starting with datAshur Pro2, which are the advantages this device offers compared to its predecessor datAshur Pro?
First of all, datAshur Pro came with a pre-configured PIN from the factory. (11-22-33-44) and there was a risk that a user was going to use only that code. With the datAshur Pro2 a user MUST create a personal PIN. Also the security was lifted to an even higher level, using a secure micro controller that is accredited Common Criteria EAL4+.
What is the capacity of datAshur Pro2? The capacity now starts with 4GB and goes up to an astonishing 512GB When do you expect the accreditation of datAshur Pro2 to Dep-V security level (equal to NATO restricted) to be completed?
The NLNCSA has started to map the differences, predicting how long it will take to perform the enhanced accreditation. We hope this will be completed in Q4.
Do you foresee an improvement in the accreditation level of datAshur Pro2?
That depends on the demand in higher areas. The NLNCSA only responds to the need of their customers, and so there has to be a demand from a government body or military body.
Is there a plan to divert the origin of manufacture of datAshur Pro2 in order to upgrade the accreditation of the product to a higher level?
There is no such plan.
Which are the potential customers of datAshur Pro2 ?
Everyone that has to protect information on several levels, including people in the field, since the datAshur Pro2 is IP58 dust and water resistant.
And now, coming to cloudAshur, what are the specifications and the advantages of this device compared to similar products available in the market?
The strongest is using a PIN. The keyboard is alphanumeric and therefore you can spell a word or sentence. Using the stand alone device key logging malware cannot reach into the authentication process and therefore this aa very strong and relatively easy way to protect your data.
How do cloudAshur encryption modules work and which services do they offer?
After configuration cloudAshur is used together with a laptop/PC/Mac. Once the personal PIN is entered, the user has to login to the cloudAshur client, with their username/password, and then they are connected to whichever cloud service they use. During the synchronization process the data is being encrypted using the encryption key that all their colleagues use. And through the management console the Administrator can confuse a number of safety/rescue features to help the person on a distance.
Can you describe what is the Management Console?
With the Management Console the Administrator/IT manager can see a detailed overview of activities in the cloud that they are using. Who copies, who reads, who deletes. He can set a limited time of usage from the console, he can set a limited area that the cloudaAshur is working in, he can manage the licenses. You need the number of licenses according to the number of cloudAshur encryption modules that you have. Master keys and slave keys are the same hardware.
What is the KeyWriter Software, what does it do and how does it work?
First the admin sets a variety of configuration settings, and sets the keys as master key. Then he can write the configuration file through a patented 'tunnel' to another USB port on the same device. From there, he can write up to 20 slave keys at the same time. (using a USB hub, sold though a third party).
What are your expectations for the commercial promotion of your new products to the international market?
Since this product and this solution are taking away all of the hazards of using cloud solutions, we expect this product to have a potential big impact on the cloud industry.