InfoSecurity 2019 cloudAshur: I flew over to London to see it with my own eyes...
Share
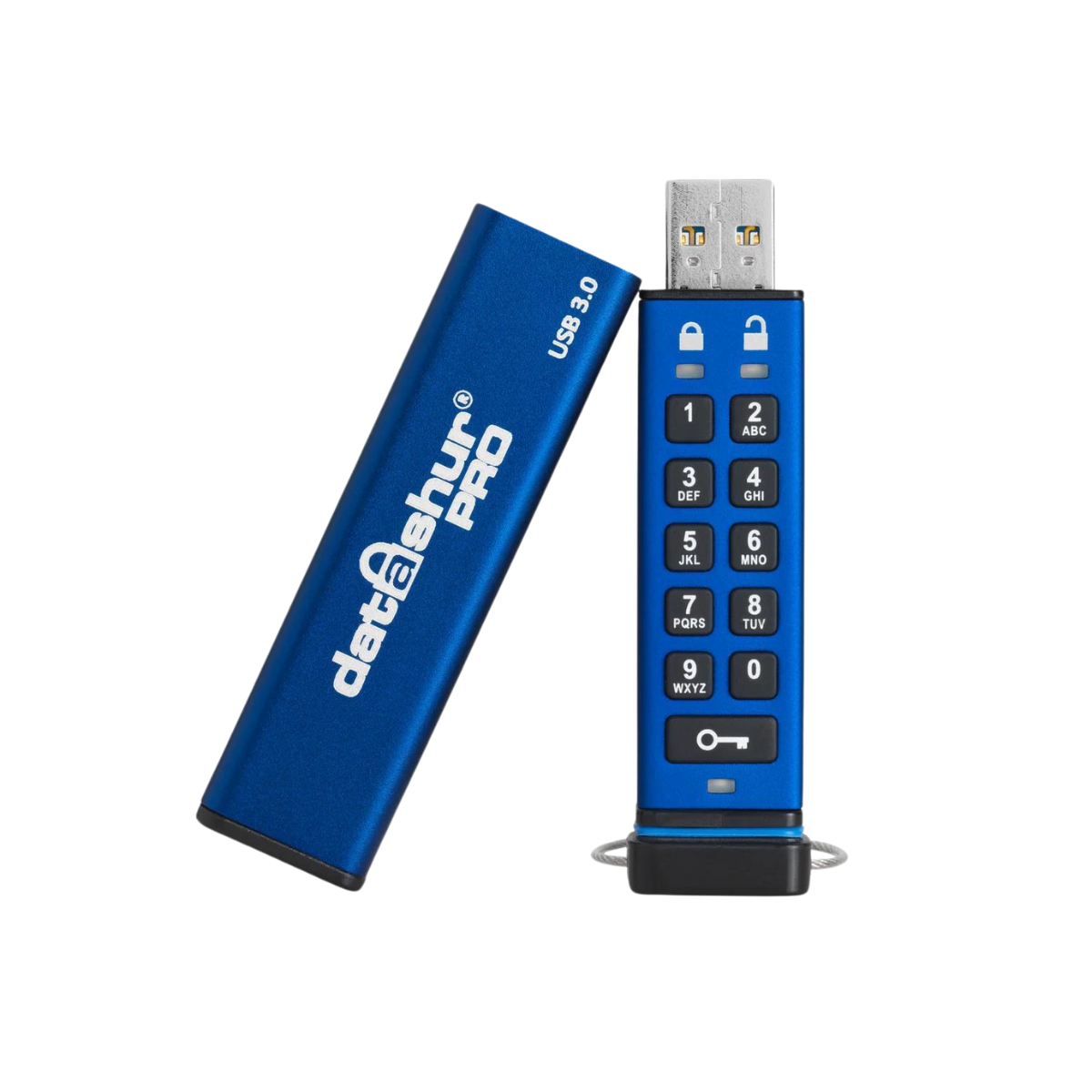
datAshur Pro2: the successor of datAshur PRO
iStorage was apparently going to announce two new products, that's reason enough to get curious and book my flight to London.
One of the new products is the datAshur Pro2 , the successor of the datAshur Pro, which currently is NATO restricted and Dep-V accredited, and so top member of the encrypted pin operated USB flash drives.
This drive holds extra security features, and reaches a maximum capacity of 512GB!
The other, most important feature is the heart of the product, the nerf center. It is equipped with a secure microprocessor that is common criteria level 5+ certified. So yes security wise it gets better and better.
cloudAshur: encryption management in your own hand
The other solution is cloudAshur. John Michael, CEO of iStorage did a public presentation and began his presentation by showing the cons and pros of cloud usage in general. Despite what managers of data centers are saying, #data #breaches are regularly in the news and companies are taking security more seriously than ever because of that and of course we have the #GDPR regulations. Their reputation is on the line and so they have to manage their data with silk gloves.
Cloud storage is being pushed by the commercial world the last couple of years, but there was a very specific reason why government usage was held back on that topic. First reason was the location of the data, which could affect local regulation about the ownership and privacy rules. Second reason was the fact that cloud providers seem to use encryption, while key management was kept in the dark. The encryption key management is probably the most valuable argument to hold back on cloud usage.
iStorage has found a way to take encryption management in your own hand, by using encryption modules that encrypt data on the fly while it's been synchronized into the cloud, regardless of which provider you use. With the management console you can then regulate access and limitation of time, and location. You can also view license usage, and it has a log overview to see who is viewing/downloading what. Theft or loss can easily be controlled by the console, to simply select 'disabled' or 'delete' depending on the applied circumstances.
Conclusion; there is a huge market that is open for solutions like cloudAshur, anabeling access and share their data from anywhere. Please contact us for questions or quotes.